Guide on how to implement Cross-Tenant Disk Encryption with Azure Kubernetes Service
This documentation is an expansion of the article "Configure cross-tenant customer-managed keys for an existing storage account" of Microsoft. It's purpose is to explain how to allow a "Disk Encryption Set" to consume a key hosted in a KeyVault from a diferent Tenant. The disk encryption set will then be used to encrypt a Kubernetes Persistent Volume Claim.
Introduction
This documentation is an expansion of the article " Configure cross-tenant customer-managed keys for an existing storage account " of Microsoft. It's purpose is to explain how to allow a "Disk Encryption Set" to consume a key hosted in a KeyVault from a diferent Tenant. The disk encryption set will then be used to encrypt a Kubernetes Persistent Volume Claim.
Tenant of KeyVault: A
Tenant of DiskEncryptionSet: B
All the steps outlined in this documentation will assume that you have Owner access in both Tenants.
During the creation of the objects, unless otherwise specified, we have used the default values prompted by Azure. Feel free to adjust according to your needs.
Implementation
Step I: Create the key vault in tenant A
A) Connect to the tenant
az login --tenant A
B) Set the subscription:
az account set --subscription <your sub>
C) Create the Resource Group (feel free to adjust name and location):
az group create --name rg-for-demo-vault --location NorthEurope
D) Create the key vault:
az keyvault create -n rg-for-demo-vault -g rg-for-demo-vault -l NorthEurope --enable-purge-protection true
E) Create a key in the key vault:
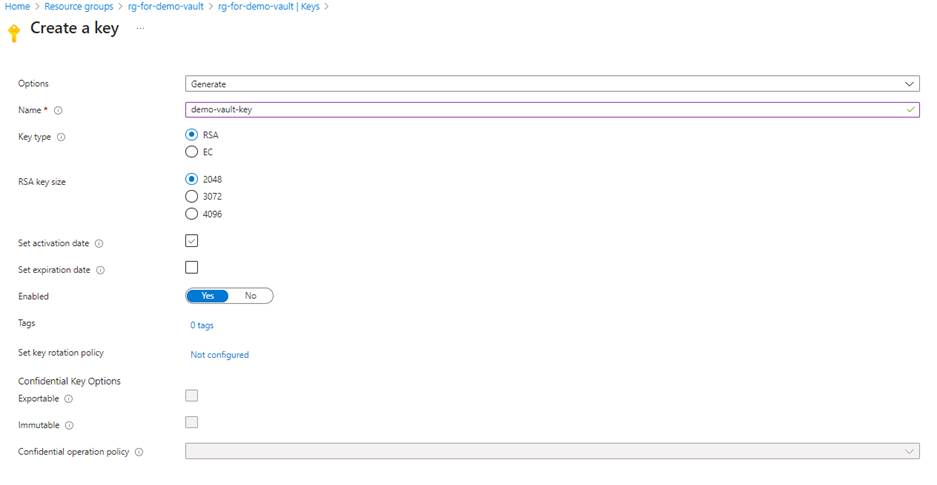
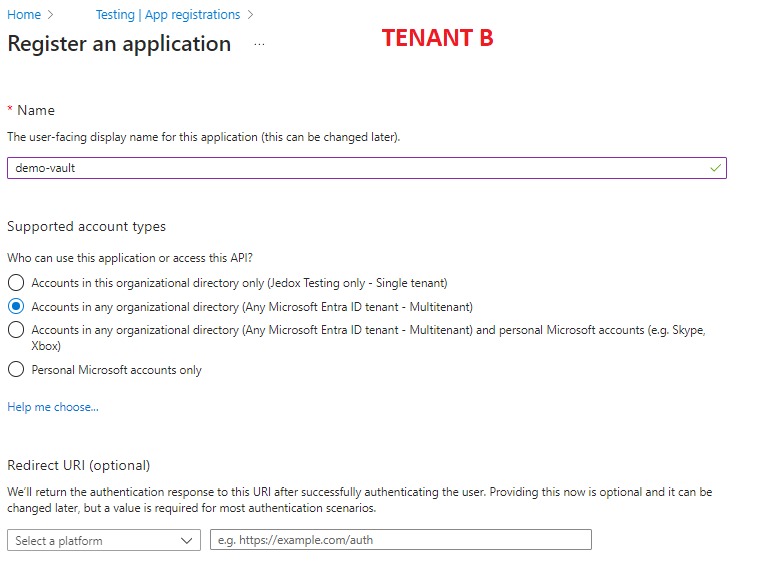
Step II: Create the App registration in Microsoft Entra of tenant B
Make sure to check " Accounts in any organizational directory (Any Microsoft Entra ID tenant - Multitenant) "
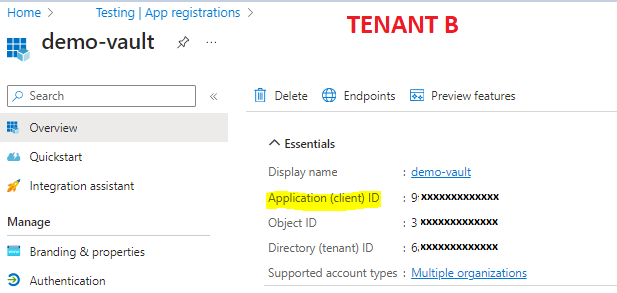
Retrieve the "Application (client) ID" of the "demo-vault" app. We will need it for the next step.
Step III: Create a Service Principal in tenant A then assign it to the KeyVault
A) Create the ServicePrincipal (make sure that before you issue the command, you're still in the context of Tenant A:
az ad sp create --id "Application (client) ID"
Once you issue the command, a new service principal will be created in Tenant A. You should find it in Tenant A under the same name as you used in the creation of the AppRegistration in tenant B:
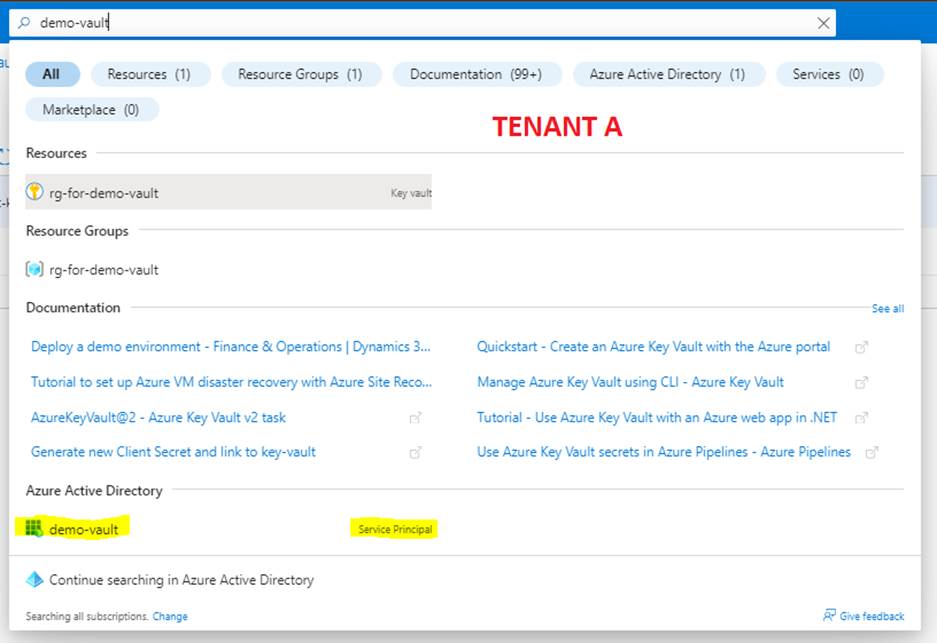
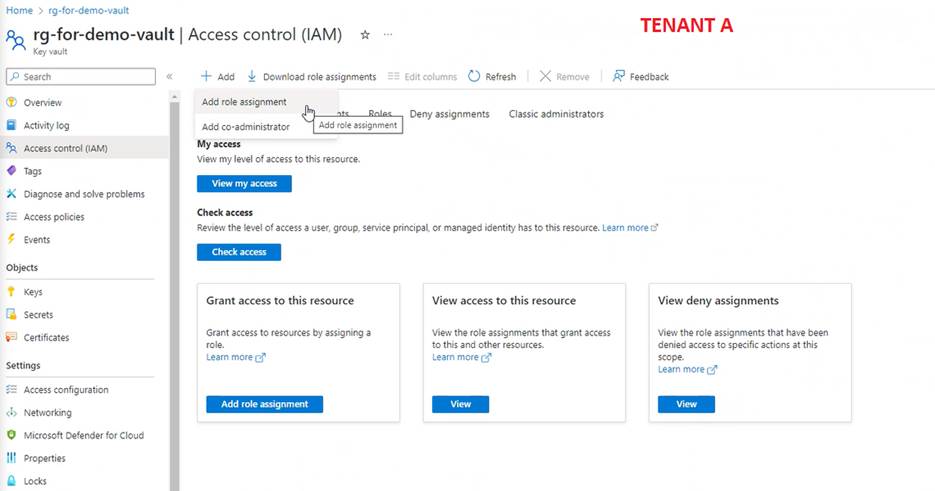
B) Grant the service principal rights to the key vault:
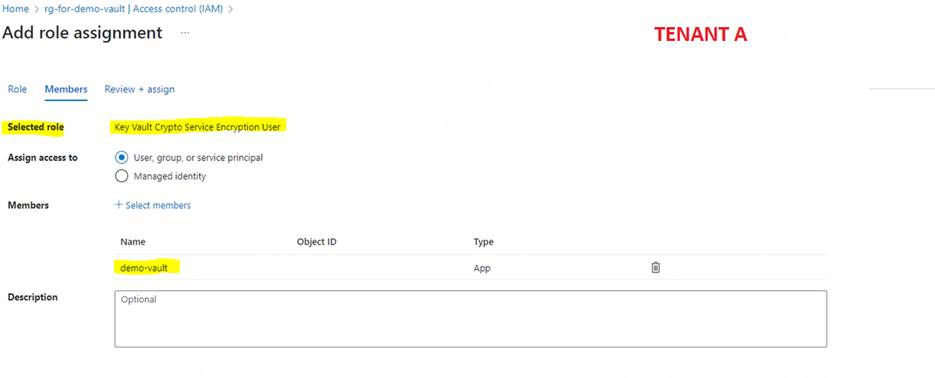
Select the role "Key Vault Crypto Service Encryption User":
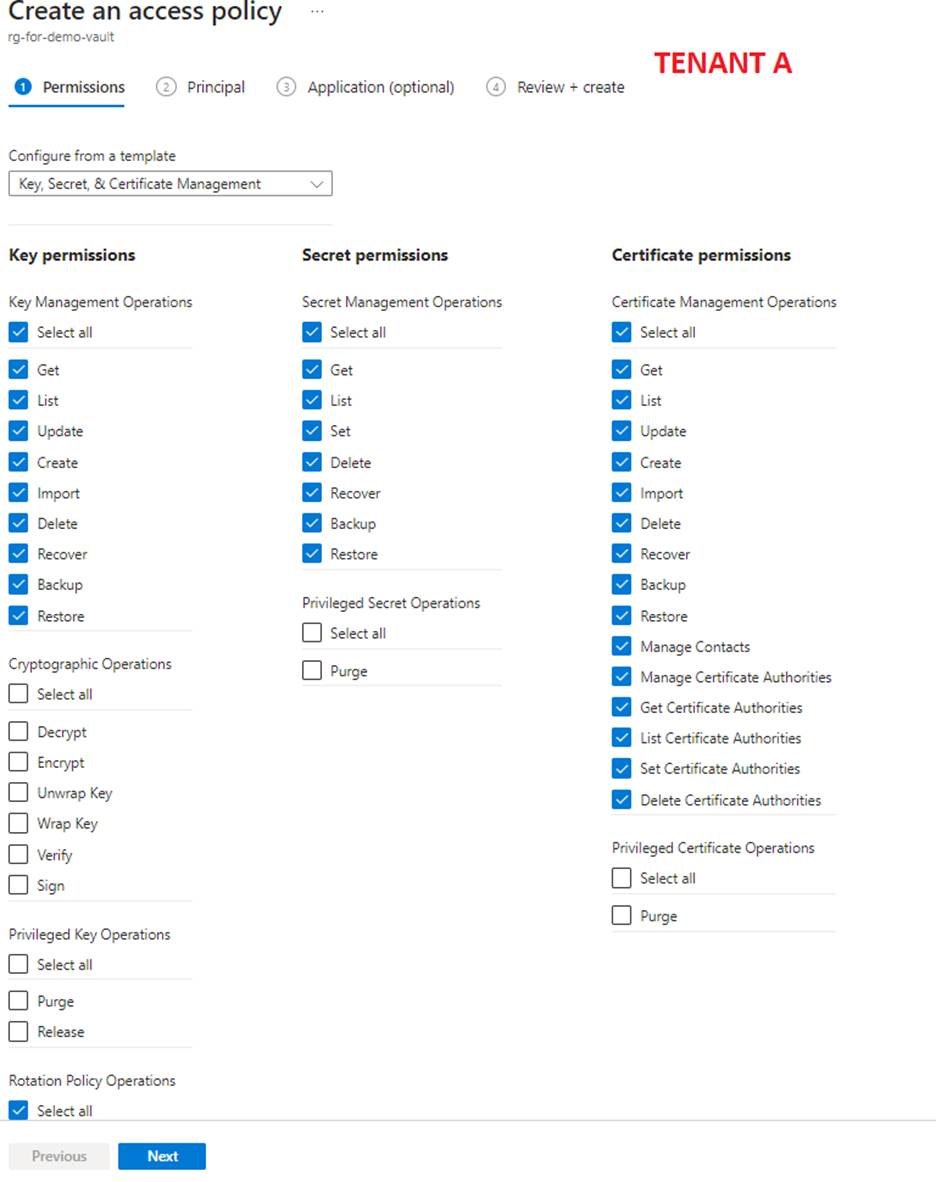
C) Go to "Access Policies" of the Key Vault and create a new policy.
At step 1, select the right permissions for you:
At step 2 add the service principal:
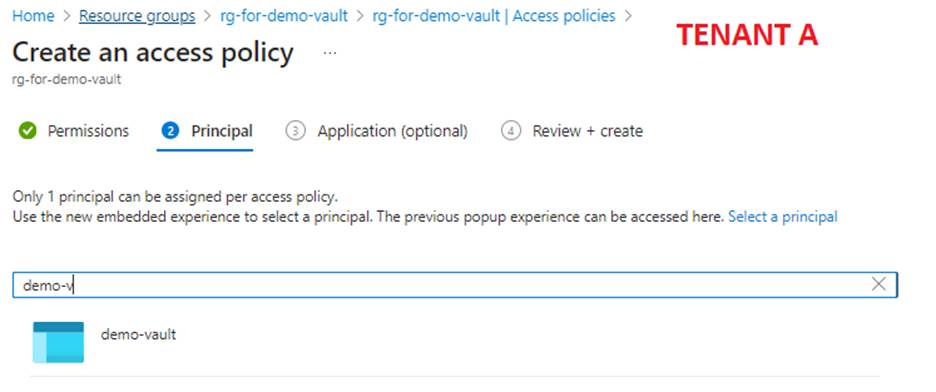
Rest of the points remain default. Then create the policy. In the end you should end up with:
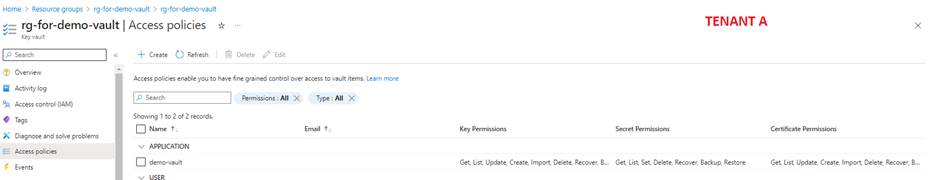
Step IV: Create the disk encryption set in Tenant B
Note: For the purpose of our demo, we have created the Managed Identity and DiskEncryptionSet in the Infrastructure Resource Group of the cluster where we are going to consume the encrypted PVCs.
- Create an "User Assigned managed identity":
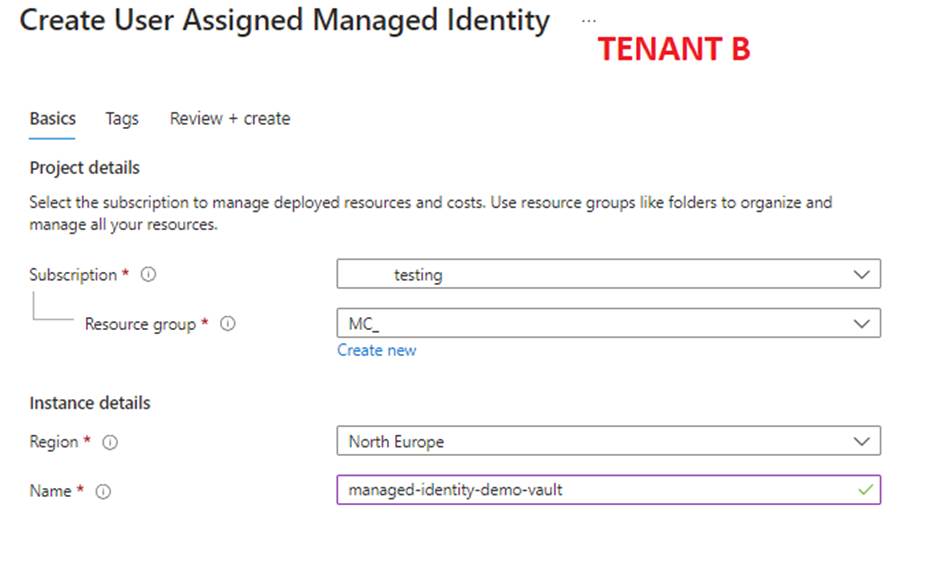
- Assign the Managed Identity to the App registration in Microsoft Entra of tenant B:
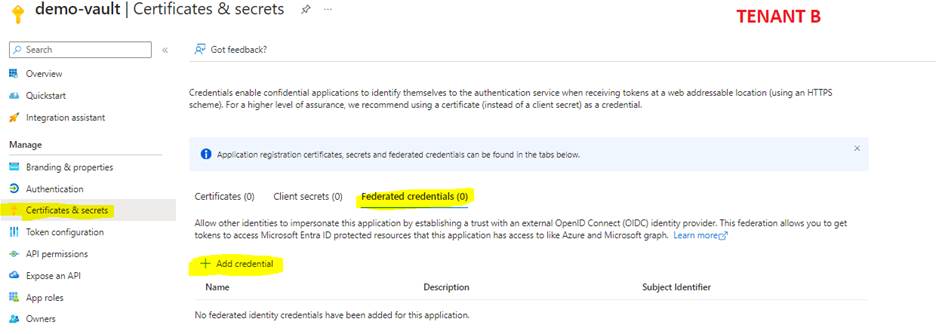
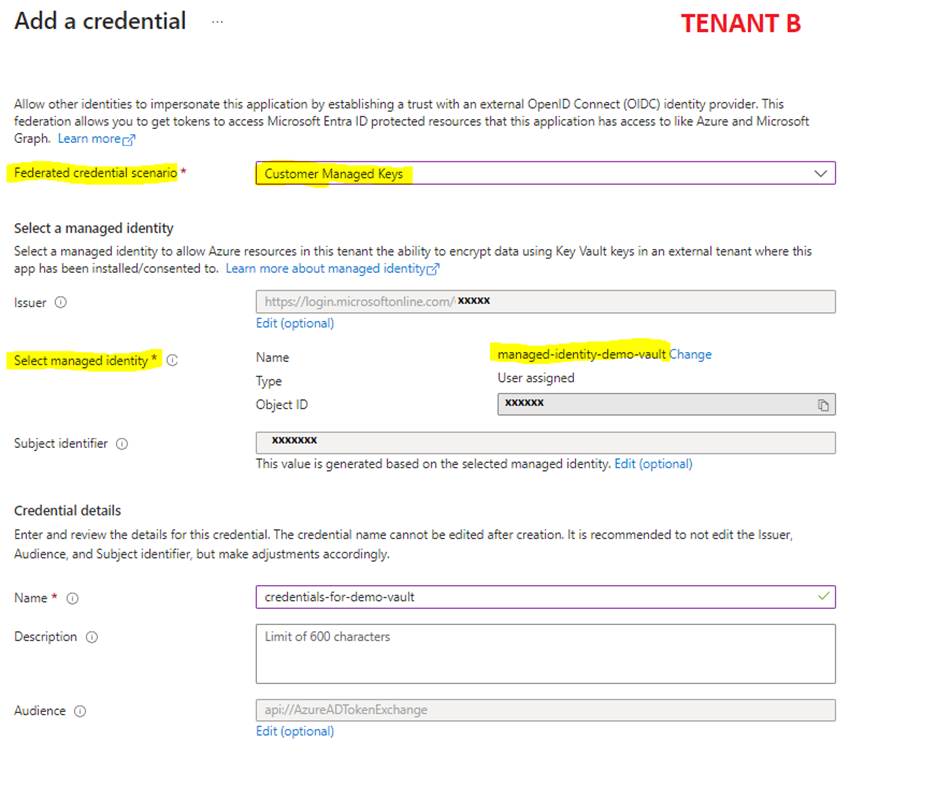
Make sure to choose the "CustomerManagedKeys" for the federated credential scenario.
Make sure to choose the correct managed identity for the "select managed identity".
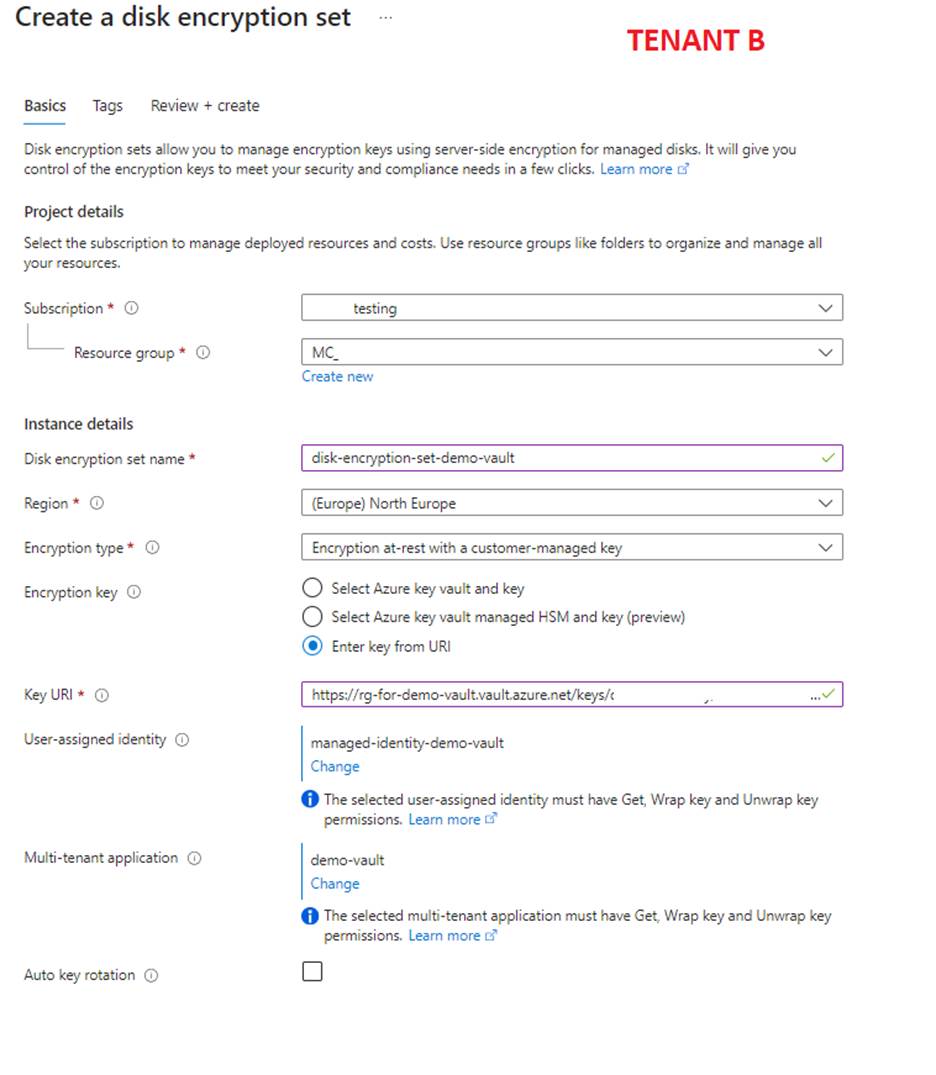
- Create the Disk Encryption Set inside the Infrastructure Resource Group "MC" of the Cluster:
The key URI must be taken from the Key Vault;
The "User Assigned Identity" must be the identity you created earlier;
The "Multi-Tenant application" should be the one you created earlier;
Step V: Create a storage class in your Kubernetes cluster that will provision encrypted disks.
kind: StorageClass
apiVersion: storage.k8s.io/v1
metadata:
name: azure-byok
provisioner: disk.csi.azure.com # replace with "kubernetes.io/azure-disk" if aks version is less than 1.21
parameters:
skuname: StandardSSD_LRS
kind: managed
diskEncryptionSetID:/subscriptions/XXXXX/resourceGroups/XXXX/providers/Microsoft.Compute/diskEncryptionSets/disk-encryption-set-demo-vault
reclaimPolicy: Retain
Create a PVC that will consume the StorageClass
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: azure-byok-pvc
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 4Gi
storageClassName: azure-byok
volumeMode: Filesystem
Conclusion
The documentation delineates the process of establishing a cross-tenant disk encryption setup utilizing Azure Kubernetes Service (AKS). By orchestrating a Disk Encryption Set to access a key from a Key Vault in a different Tenant, and aligning it with a Kubernetes Persistent Volume Claim, a robust encryption infrastructure is realized.
This configuration ensures secure encryption of sensitive data housed in Persistent Volume Claims, meeting stringent security and compliance mandates. All the steps outlined in this document provide a roadmap towards deploying a secure, cross-tenant disk encryption framework within Azure, thereby significantly bolstering the security measures surrounding your Kubernetes deployments.
A minimal admission controller
Mar, 2023 Yalos Team
Writing such a controller is as simple as writing any other controller. This post helps avoiding common pitfalls on coding your first one. With working code.
read